Dear CloudTards: "Securing" The Cloud isn't the problem…
@GeorgeResse pointed out this article http://www.infoworld.com/d/cloud-computing/five-facts-every-cloud-computing-pro-should-know-174 from @DavidLinthicum today. And from a Cloud advocate point of view I like four of the assertions. But his point about Cloud Security is off:
“While many are pushing back on cloud computing due to security concerns, cloud computing is, in fact, as safe as or better than most on-premises systems. You must design your system with security, as well as data and application requirements in mind, then support those requirements with the right technology. You can do that in both public or private clouds, as well as traditional systems.”
In a sense, David is right, the ability to develop a relatively secure computing architecture in a cloud environment, in theory, may be reasonably similar to “traditional” computing. But there’s two things I hate about this paragraph. First, it seems to reflect this naive notion that systems are deployed secure until vulnerability happens. Second, it completely misses the issue facing security management. The problems facing management re: The Cloud have nothing to do with ability to architect “secure”. They have to do with the ability to manage risk.
A Primer About Information Security and Risk Management
Security, at its fundamental core, is not problem of poor network architecture development or poor software development practices. Security is a problem of behaviors, those having to do with the interrelation of systems and people. Managing risk is related, but very different in it’s nature. Information risk management is a problem of information quality and decision making around those behaviors. Information risk management requires:
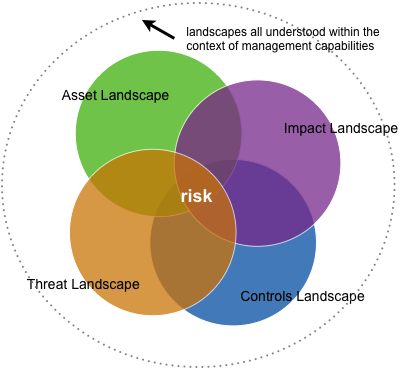
- Knowledge about the asset landscape – Data from what studies we do have about data breaches and successful IT operations strongly correlate visibility (even the degree of visibility) and variability in the asset landscape to success and failure in IT and IT security.
- Knowledge about the threat landscape – types, frequency, strength, capability, and adaptability of the threat agents are among the bits of information required to know and understand risk.
- Knowledge about the controls landscape – control information is the ability to resist threats, so not just the technical feasibility of resistance, but also the operational (human skills/resources) contributions to that ability to resist.
- Knowledge about the impact landscape –impact information from pressures within the organization (things like response costs, downtime, and productivity losses) and from outside the organization (compliance fines, legal judgments, the consequences of IP loss, brand damage…).
In addition, there’s knowledge we synthesize when we consider one landscape in the context of another (vulnerability might be said to be the a state we develop when we consider threat, asset, and control landscape information, risk is what we understand when we consider the information we have from all four). In the diagram, it’s where the circles overlap.
I’m sorry if this is basic for many of you readers out there, but I thought this content was necessary – because it’s obvious cloud architect types are obsessing over the ability to build a similar technical environment without understanding the basics of managing risk.
What Really Bugs Security Managers About Cloud Computing
So the issue with moving to “the cloud” for a CISO has to do with two basic things:
- Information quality
- Responsibility (data ownership in CISSP terms).
For information quality, we are concerned with:
- A – The ability to get reasonably similar information for the technical behavior information of our systems, and
- B – The human behavior information from both the threat and the controls landscape.
For Responsibility, we are concerned with:
- If the information is bad news, who is repsonsible for what actions?
- Given threat execution (the bad news isn’t just an attack, it’s a compromise) When a data breach occurs, where will the buck ultimately stop?
For that last bullet, PCI is sort of establishing a “case law” for us already. The lesson to take away from the experiences of others is this: Following the suggestions of CSA documents and Cloud Audit information (excellent, necessary, and as useful as that documentation is/will be) isn’t going to be enough to manage risk in the cloud with the same quality as “traditional” architectures for many people. And it looks like you will be left as “custodians” of the data regardless of who is paying the W-2 of the guy at the SEIM console. More colloquially, “Crap will continue to run downhill, you’ve just diverted it a ways upstream.”
Takeaways
The objections to cloud adoption from an information risk management standpoint have nothing to do with the ability to engineer “secure”. It is about an ability to manage risk. There’s a significant difference there that this sort of advocacy continues to gloss over. Of course, given how nascent information security and information risk managent are as disciplines, however, if you can transfer full responsibility to a cloud provider who is stupid enough to believe things like “we can secure your systems better than you can”, I say go for it!
Ack.
Completely agree with this – I only wish others would see that assumption of risk isn’t just application centric.
Well said. I like to think the same way when people talk about anything cloud related. Security, compliance, data mapping…
People assume that the cloud will be so different. It is but not in the basic principal ways we are missing right now.