Cool Tech Not at RSA
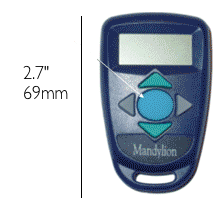
Quick! Someone get these folks a marketing department! Someone showed me a cool password storage token from Mandylion Labs. You can load passwords over a little electronic interface, and then keep long lists of superuser passwords in your pocket. I had to mail my buddy to get their name. It seems somewhat better than a printed list, in that you can electronically manage loading passwords onto it. The downside is you can’t swallow it when you’re captured by the enemy.
Cute. Along similar lines, have you seen this for dealing with credit/atm/discount cards? http://www.chameleonnetwork.com/pocket.htm. Imagine the power of one of these along with say access to choicepointe….
-DM
Though I have to say, it limits you to 14 characters? That’s lame, so much for any passphrases….
-DM
how many chars do you want to enter with 4 buttons?
Why not just use GnuKeyring.
1) Doesn’t fit in my pocket
2) It’s easier to own a network connected device.
Greetings Adam. Thank you for the flattering comments on our technology. The essence of our token is that it is a password generator and memory aid – it manages up to 50 simultaneous login records (system name, password & policy for login (lenght composition, expiration) and user ID. We do need a marketing department!!! As evidenced by the reply comments to your post, we are so misunderstood. All we are is a keychain sized device that aids a user in the generation, storage and recall of thier passwords. Nothing more, nothing less. We are air gapped from any system and work instantly. —
One Last thing. — You dont have to swallow if caught by the enemy — For two reasons, A) it has a destroy function- that if the number of tries to enter is exceeded (ie 3 tries of the finger pattern) you can set the sanction – ie shut off for 15 minutes, 1 hr, 24 hrs or destroy ) (both number of tries and sanction u can set) — and B) if used in accordance with some concepts of operation (conop) emerging out of the military- it is used as a memory aide – so that the password is not stored in the token – even if the bad guys get through all the defense in depth layers — its still a hollow victory — its not the password — but something the user looks at re recall (ie something they know – applied to the displayed code) the actual password — i.e. displayed and generated password is #Xe$&g1^ — but since i read all my passwords backwards — the actual password that i only know is ^1g&$eX# — there are a million variations to this offset approach – ie starting at the second character – leaving out a character – adding your initials etc etc — again part of the defense in depth of using the token – its a common sense way of being able to competently manage multiple cryptographically strong passwords — and like your very appropriate comments on identity theft — the experts really dont have a clue – because what it takes is common sense and a little viligence on the part of the user – both of which cannot be monetarized by the big security companies with proprietary solutions!!!
regards
joe grajewski
Only 50? That seems rather low for either my personal use (I have about 150 passwords in my Mac’s KeyChain) or corporate use (where a sysadmin may have access to hundreds of computers for occaisonal fixing duty.)
I’d think that with the cost of ram where it is, never ever having to have a conversation about “is that enough” would be cheaper than those conversations.
Re: 14 characters. Well my PGP passphrase is 43 characters long…..
-DM
Adam – please email – i would love to continue the conversation offline-i appreciate the attention our web site is getting — you are very well read — but to publicly answer your question on 50 logins – we use non-volatile memory (and memory within the processor core) which is more expensive then flash — our memory is basically hard wired and not effected by electrical charge -its way more than a flash thumb drive in complexity — also and in addition to being potted etc our memory/processor- cannot be erased or imaged externally – the big thing more than anything else is you get more than 50 records on a keychain and you got too many eggs in one basket -( why not have two or more and color code them – red for network components etc – ) also if u get more than 50 records – scrolling and indexing etc (especially because its only got 5 keys) becomes a nightmare on the user interface side –