Does It Matter If The APT Is "New"?
As best as I can describe the characteristics of the threat agents that would fit the label of APT, that threat community is very, very real. It’s been around forever (someone mentioned first use of the term being 1993 or something) – we dealt with threat agents you would describe as “APT” at MicroSovled when I was there in 2001-2005. We dealt with it as a firewall vendor at Progressive Systems in 1998. This isn’t a “is the APT real?” blogpost.
That said, I wanted to talk about why there should be still more discussion around the APT. Hogfly at the Forensic Incident Response blog asks:
“What should matter is how successful they have been. What should matter is defending ourselves. What should matter is how and where we share this information. What should matter is taking this information to those with the ability to do something about it. What should matter is taking the fight to the enemy.
So I ask again, does it matter if this threat is new?”
My response is that it actually matters very much.
We are hearing a new label. Whether the label originated from “the cool kids” or not, it’s being co-opted by marketing. And right now, we’re sort of in this important window of trying to get some understanding, some significant amount of intersubjectivity about what the APT is and what it means to a broader audience. Once that’s established, then we can try to understand what to do. But why does it matter if the threat is new or old?
There is a significant increase in the use of the term. When it’s a BusinessWeek cover story (2008, btw), it gets seen by people. What we need to understand is if this “new” visibility is the result of either a change in the threat landscape or a change in the marketing landscape.
IS APT A SHIFT IN FREQUENCY, A SHIFT IN CAPABILITY, OR A SHIFT IN BOTH FREQUENCY AND CAPABILITY?
If it is a change in the threat landscape, we need to understand what aspect of the landscape is changing. The shift could be said to be one of a few scenarios:
1.) More attacks on the same targets by the same actors. That is, is the government, defense industrial base, or other targets attractive to certain nation-states are experiencing a new amount of threat events.
2.) More attacks on new targets by the same actors. That is, are the nation-state actors finding new targets? If so, are their targets of choice changing from organizations that are antagonistic to the policy desires of the sponsor state (certainly the Mandiant report reads like the Chinese are after anyone who threatens their political stability), to other targets – like retailers or hospitals (has, as Mandiant says, the APT become *everyone’s* problem)?
3.) More attacks on the same targets by new actors. That is, it’s not just the usual suspects. If *this* is the case, then we’re seeing a fundamental shift in the capabilities of threats. That is, bad guys who used to be dumb just got a lot smarter thanks to the dissemination of skills/resources (sharing of technique, new access to advanced toolsets, etc) and they are going after all those people who were worrying about the APT in 2003.
4.) More attacks on new targets by new actors. That is, the bad guys who used to be dumb just got a lot smarter and are now trying to use their new smarts against victims who heretofore had not had to worry about the APT.
Finally, the other option is that there is no shift in frequency or capability, but there is a shift in marketing budgets. I tried to run a google trend on “Advanced Persistent Threat” but got:
Your terms – “Advanced Persistent Threat” – do not have enough search volume to show graphs.
And “APT” trend search was clouded by other things that shared the same TLA.
WHAT DO YOU THINK?
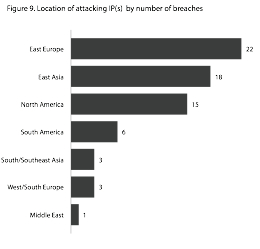
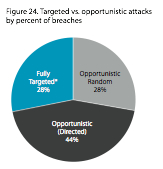
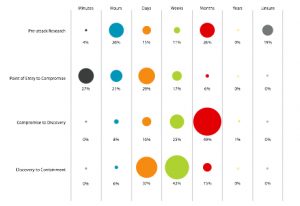
I’m not sure what we’re seeing. I was personally disappointed by the Mandiant report’s lack of demographics and frequency information. I’m ready to believe that we’re seeing a fundamental shift in distributions concerning the threat agents, but there wasn’t anything in the report to support that notion. I will leave you with a couple of items from the Verizon Report, though, and I’ll let you draw your own conclusions, given that the Verizon data set isn’t heavy on what we might call the Defense Industrial Base – those folks already live and breathe this stuff – and this data is from 2008.
SOURCE OF ATTACKING IP
TARGETED VS. OPPORTUNISTIC ATTACKS
TREND IN USE OF CUSTOMIZED MALWARE
TIME TO DISCOVERY

The minute you connect your machine to the Internet you’re up against a “persistent threat.”
Gotta love marketing spin. There have been stories of security product vendors wanting to tie anything and everything to China in order to show that they’re on top of it and you should buy their products. More snake oil and product vendors forget that it’s still humans that do the bulk of the analysis and defensive ops.
I’m still keeping an eye out for that magical “silver bullet” of security! 😉
-Jerry
Pretty sure the Chinese didn’t invent industrial espionage