High Assurance Certificates and the Fake NEC
So I’ve seen the story in a bunch of places, but something about Bruce Schneier’s posting on “Counterfeiting an Entire Company” made me think about certificates, and the green URL bar.
In the name of NEC, the pirates copied NEC products, and went as far as developing their own range of consumer electronic products – everything from home entertainment centers to MP3 players. They also coordinated manufacturing and distribution, collecting all the proceeds.
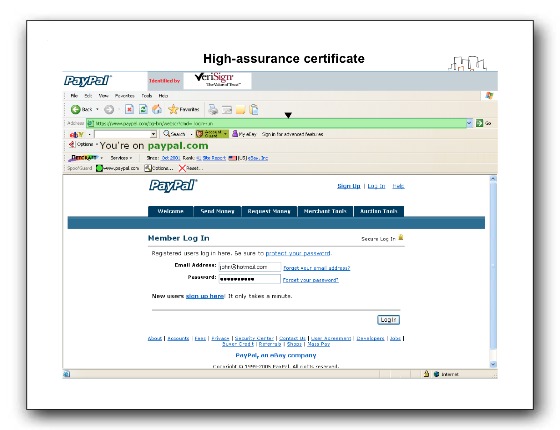
I’ve argued in “Meet The New Browser Security, Same as the Old Browser Security?,” “Build Irony In,” “Web Certificates Economics” and “‘High Assurance’ Certificates” that the high assurance certificate scheme won’t dramatically improve user resistance to phishing.
So, I’d love to hear why, in an era when criminal enterprises are able to forge an entire enterprise, to the extent of developing new products, they won’t do enough to get a high assurance certificate?
Now, you can argue that this is bar-raising, and I’m allowing perfection to be the enemy of the good. That’s a fair argument, which deserves refuting. After the break. Also in after-the-break land, what my positive, useful proposal is. (Persistence.)
Bar raising, that is, making the attack harder to execute, is all about changing the economics of the attack. By making it more expensive, the number of attackers who will execute the attack drops for two reasons: first, the pool of attackers who have the resources to invest shrinks, and second, the ROI changes.
The ROI change depends on the investment changing more than the return. I believe that in the case of the green URL bar, the return will change dramatically. After all, there will be a push to train users to look for the green bar, and when they see it, to believe that they’re on the right site. Thus, as soon as the phisher gets over the bar, the user will be fooled.
User studies such as “Why Phishing Works” (Rachna Dhamija, J.D. Tygar, Marti Hearst) and “Do Security Toolbars Actually Prevent Phishing” (Min Wu, Robert Miller, and Simson Garfinkel) show that users are annoying, and us security people would be happier replacing them with something more predictable not responding to the designs that security experts have put forth, and that testing these designs is important. If you read the studies, note the strong method differentiation. Dhamija explicitly asked users if sites were real, Wu gave them a task where security was a secondary aspect.
I expect what will happen is users will cue on the toolbar. Phishers will notice this, and learn to get certs. We’ll end up back where we are, except the CAs and phishers will have made money from web site operators.
I expect that persistence memory about the certificate, so that your browser alerts you on change, with a design that has been created with the user in mind, and tested on a variety of real users, is the right model.
The image is of many toolbars in one browser, and is taken from Min Wu’s slides “(PowerPoint Slides) Why do anti-phishing toolbars fail and can we do better,” APWG 2006 Spring General Meeting.